Venga, vamos a ver si finalmente consigo instalar un servidor de correo que sea administrable, ya que las veces que lo he intentado siempre me he quedado a medias… vamos ahí de nuevo pues!
Partimos de una debian recién instalada (en mi caso tiro de un contenedor lxc) y actualizada.
Instalamos algunos paquetes básicos para poder usar en condiciones el sistema:
root@mail-nusepas:~# apt install vim mtr glances net-tools
A continuación las dependencias que vamos a necesitar para instalar el servidor de correo
root@mail-nusepas:~# apt install postfix postfix-mysql dovecot-core dovecot-imapd dovecot-pop3d dovecot-lmtpd dovecot-mysql mysql-server apache2 php-fpm php php-mysql php-imap libsasl2-modules libsasl2-modules-sql
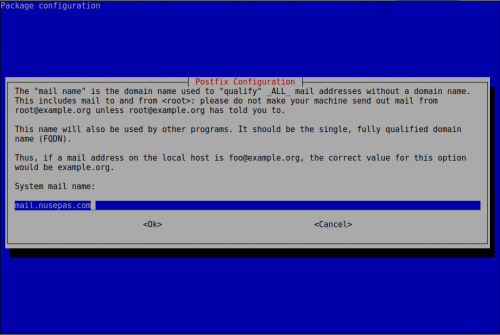
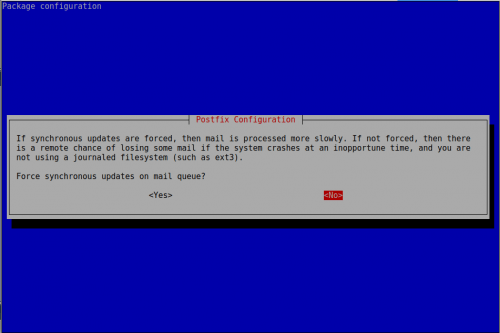
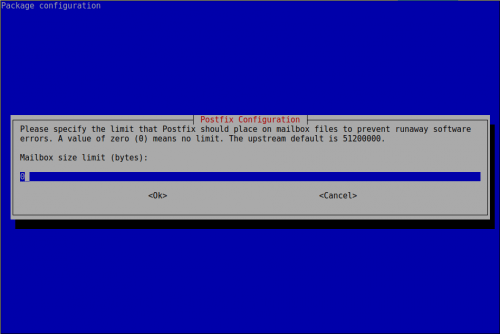
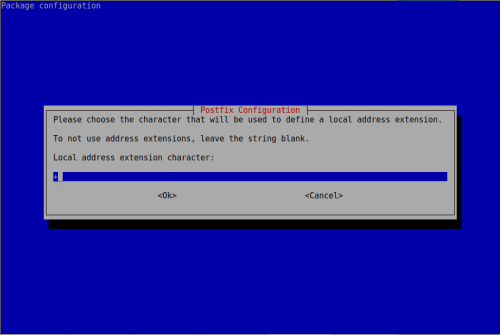
Ahora vamos a configurar postfix
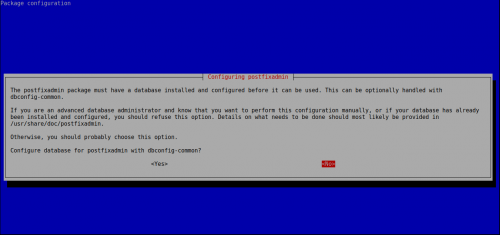
root@mail-nusepas:~# dpkg-reconfigure postfix
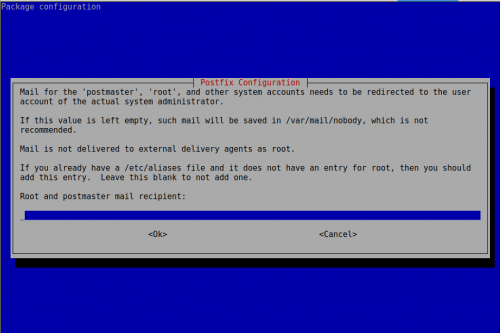
Lo dejamos vacío porque le indicaremos el correo electrónico en /etc/aliases
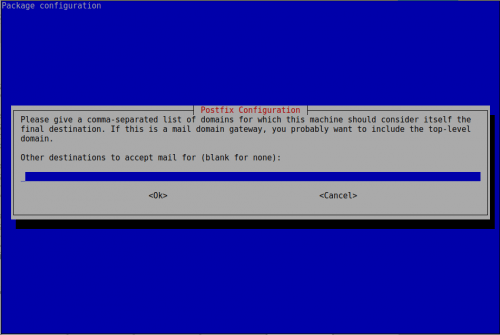
Lo dejamos vacío porque le indicaremos los virtual domains al momento de instalar el postfixadmin
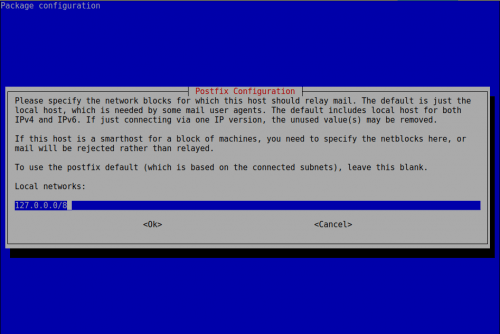
No vamos a permitir el reenvío de correos electrónicos de otros hosts de nuestra red, lo correcto sería tener un servidor de correo dedicado para los relays

De momento sólo IPv4, que con IPv6 tenía problemas con el envío de correos a gmail por ejemplo.
Ahora modificamos los aliases
root@mail-nusepas:~# vi /etc/aliases postmaster: root webmaster: root root: [email protected]
Postfixadmin
Ahora vamos a descargar la última versión del paquete .deb de postfixadmin y lo instalamos
root@mail-nusepas:~# wget https://netix.dl.sourceforge.net/project/postfixadmin/postfixadmin/postfixadmin-3.2/postfixadmin_3.2-1_all.deb root@mail-nusepas:~# dpkg -i postfixadmin_3.2-1_all.deb root@mail-nusepas:~# apt -f install
En la configuración le indicamos que no
Ahora vamos a configurar la base de datos y postfixadmin
root@mail-nusepas:~# mysqladmin -p create postfix Enter password: root@mail-nusepas:~# mysql -p postfix Enter password: MariaDB [postfix]> GRANT ALL PRIVILEGES ON postfix.* TO 'postfix_admin'@'localhost' IDENTIFIED BY 'XXX'; Query OK, 0 rows affected (0.00 sec) MariaDB [postfix]> FLUSH PRIVILEGES; Query OK, 0 rows affected (0.00 sec) MariaDB [postfix]> Bye
Ponemos la configuración de la base de datos en el fichero de configuración de postfixadmin:
root@mail-nusepas:/etc/postfixadmin# vi dbconfig.inc.php $dbuser='postfix_admin'; $dbpass='gfQnxfRc59PzrgaK'; $basepath=''; $dbname='postfix'; $dbserver='localhost'; $dbport='3306'; $dbtype='mysql';
Ahora vamos a configurar apache para poder acceder a la administración web de postfixadmin, al mismo momento aprovecharemos para configurar los certificados SSL.
root@mail-nusepas:~# vi /etc/apt/sources.list deb http://ftp.debian.org/debian stretch-backports main root@mail-nusepas:~# apt update root@mail-nusepas:~# apt install python-certbot-apache -t stretch-backports root@mail-nusepas:~# certbot --apache certonly Saving debug log to /var/log/letsencrypt/letsencrypt.log Plugins selected: Authenticator apache, Installer apache Enter email address (used for urgent renewal and security notices) (Enter 'c' to cancel): [email protected] ------------------------------------------------------------------------------- Please read the Terms of Service at https://letsencrypt.org/documents/LE-SA-v1.2-November-15-2017.pdf. You must agree in order to register with the ACME server at https://acme-v01.api.letsencrypt.org/directory ------------------------------------------------------------------------------- (A)gree/(C)ancel: A ------------------------------------------------------------------------------- Would you be willing to share your email address with the Electronic Frontier Foundation, a founding partner of the Let's Encrypt project and the non-profit organization that develops Certbot? We'd like to send you email about our work encrypting the web, EFF news, campaigns, and ways to support digital freedom. ------------------------------------------------------------------------------- (Y)es/(N)o: N No names were found in your configuration files. Please enter in your domain name(s) (comma and/or space separated) (Enter 'c' to cancel): mail.nusepas.com Obtaining a new certificate Performing the following challenges: http-01 challenge for mail.nusepas.com Enabled Apache rewrite module Waiting for verification... Cleaning up challenges IMPORTANT NOTES: - Congratulations! Your certificate and chain have been saved at: /etc/letsencrypt/live/mail.nusepas.com/fullchain.pem Your key file has been saved at: /etc/letsencrypt/live/mail.nusepas.com/privkey.pem
Ahora configuramos los sites de apache y le indicamos donde se encuentra nuestro certificado recién creado
root@mail-nusepas:~# vi /etc/apache2/sites-available/default-ssl.conf SSLCertificateFile /etc/letsencrypt/live/mail.nusepas.com/fullchain.pem SSLCertificateKeyFile /etc/letsencrypt/live/mail.nusepas.com/privkey.pem SSLCertificateChainFile /etc/letsencrypt/live/mail.nusepas.com/fullchain.pem root@mail-nusepas:~# a2ensite default-ssl Enabling site default-ssl. To activate the new configuration, you need to run: systemctl reload apache2 root@mail-nusepas:~# a2enmod ssl Considering dependency setenvif for ssl: Module setenvif already enabled Considering dependency mime for ssl: Module mime already enabled Considering dependency socache_shmcb for ssl: Enabling module socache_shmcb. Enabling module ssl. To activate the new configuration, you need to run: systemctl restart apache2 root@mail-nusepas:~# systemctl reload apache2
Ahora vamos a ésta url y esperamos a que se creen las tablas y todo lo necesario (tardará un rato)
https://mail.nusepas.com/postfixadmin/setup.php
Si te da problemas prueba las siguientes cosas
root@mail-nusepas:/usr/share/postfixadmin/public# chown -R www-data:www-data * root@mail-nusepas:/usr/share/postfixadmin# ln -s /etc/postfixadmin/config.inc.php config.local.php
Recuerdo que cada vez que ejecutes el setup.php deberás borrar todas las tablas creadas en la base de datos postfix (drop database postfix; create database postfix;)
Si todo está OK, nos pedirá el password para acceder a configurar postfixadmin y también para generar el hash que tendremos que poner en el fichero de configuración de postfixadmin
root@mail-nusepas:/usr/share/postfixadmin# vi config.local.php $CONF['setup_password'] = 'XXX';
Y ahora ya podremos entrar con nuestro usuario y contraseña!
Postfix
Ahora vamos a seguir realizando los pasos para configurar postfix.
Primero creamos el usuario vmail que va a ser el que va a acceder a los correos electrónicos de los usuarios
root@mail-nusepas:/etc/postfix# groupadd -g 4001 vmail root@mail-nusepas:/etc/postfix# useradd -d /var/mail -m -u 4001 -g 4001 vmail useradd: warning: the home directory already exists. Not copying any file from skel directory into it. root@melatonina:/etc/postfix# chown -R vmail:vmail /var/mail
Ahora editamos el fichero de configuración de postfix
root@mail-nusepas:/etc/postfix# cp main.cf{,.orig}
root@mail-nusepas:/etc/postfix# vi main.cf
# See /usr/share/postfix/main.cf.dist for a commented, more complete version
smtpd_banner = $myhostname ESMTP $mail_name (Debian/GNU)
biff = no
# appending .domain is the MUA's job.
append_dot_mydomain = no
# Uncomment the next line to generate "delayed mail" warnings
#delay_warning_time = 4h
alias_maps = hash:/etc/aliases
alias_database = hash:/etc/aliases
myhostname = mail.nusepas.com
myorigin = mail.nusepas.com
mydestination = $myorigin,
localhost.$myhostname,
localhost.$mydomain, ,
localhost
relayhost =
mynetworks = 127.0.0.0/8 [::ffff:127.0.0.0]/104 [::1]/128
inet_interfaces = all
recipient_delimiter = +
myorigin = /etc/mailname
mailbox_size_limit = 0
inet_protocols = ipv4
#User vmail
virtual_uid_maps = static:4001
virtual_gid_maps = static:4001
virtual_mailbox_base = /var/mail
#Configuracion mysql
virtual_mailbox_domains = mysql:/etc/postfix/sql/mysql_virtual_mailbox_domains.cf
virtual_mailbox_maps = mysql:/etc/postfix/sql/mysql_virtual_mailbox_maps.cf
virtual_alias_maps = mysql:/etc/postfix/sql/mysql_virtual_alias_maps.cf
relay_domains = mysql:/etc/postfix/sql/mysql_relay_domains.cf
#Configuracion de SSL/TLS con los archivos de certificados
smtpd_tls_cert_file=/etc/letsencrypt/live/mail.nusepas.com/fullchain.pem
smtpd_tls_key_file=/etc/letsencrypt/live/mail.nusepas.com/privkey.pem
smtpd_use_tls=yes
smtpd_tls_auth_only = yes
#Configuracion de sasl
smtpd_sasl_type = dovecot
smtpd_sasl_path = private/auth
smtpd_sasl_auth_enable = yes
broken_sasl_auth_clients = yes
smtpd_sasl_security_options = noanonymous
#Restricciones para recibir correos
smtpd_recipient_restrictions =
permit_mynetworks,
permit_sasl_authenticated,
reject_unauth_destination,
reject_non_fqdn_hostname,
reject_non_fqdn_sender,
reject_non_fqdn_recipient,
reject_unauth_destination,
reject_unauth_pipelining,
permit
# El valor debe calcularse en KB pero no de forma exacta.
message_size_limit = 102400000
mailbox_size_limit = 102400000
virtual_mailbox_limit = 102400000
#Forzado de protocolo ipv6 para que gmail no nos de problemas a la hora de enviarles correos
inet_protocols = ipv4
#Ip del servidor de correo por la que se quieran enviar los correos
#smtp_bind_address = 1.1.1.1
Configuramos la conexión con la base de datos
MariaDB [postfix]> GRANT SELECT ON postfix.* TO 'postfix_ro'@'localhost' IDENTIFIED BY 'YYY'; root@mail-nusepas:/etc/postfix/sql# vi mysql_virtual_mailbox_domains.cf hosts = 127.0.0.1 user = postfix_ro password = YYY dbname = postfix query = SELECT domain FROM domain WHERE domain='%s' and backupmx = 0 and active = 1 root@mail-nusepas:/etc/postfix/sql# vi mysql_virtual_mailbox_maps.cf hosts = 127.0.0.1 user = postfix_ro password = YYY dbname = postfix query = SELECT maildir FROM mailbox WHERE username='%s' AND active = 1 root@mail-nusepas:/etc/postfix/sql# vi mysql_virtual_alias_maps.cf hosts = 127.0.0.1 user = postfix_ro password = YYY dbname = postfix query = SELECT goto FROM alias WHERE address='%s' AND active = 1 root@mail-nusepas:/etc/postfix/sql# vi mysql_relay_domains.cf hosts = 127.0.0.1 user = postfix_ro password = YYY dbname = postfix query = SELECT domain FROM domain WHERE domain='%s' and backupmx = 1
Añadimos el usuario postfix al grupo sasl
root@mail-nusepas:/etc/postfix/sql# adduser postfix sasl Adding user `postfix' to group `sasl' ... Adding user postfix to group sasl Done.
Seguimos con master.cf
root@mail-nusepas:/etc/postfix# cp master.cf{,.orig}
root@mail-nusepas:/etc/postfix# vi master.cf
#
# Postfix master process configuration file. For details on the format
# of the file, see the master(5) manual page (command: "man 5 master" or
# on-line: http://www.postfix.org/master.5.html).
#
# Do not forget to execute "postfix reload" after editing this file.
#
# ==========================================================================
# service type private unpriv chroot wakeup maxproc command + args
# (yes) (yes) (yes) (never) (100)
# ==========================================================================
smtp inet n - - - - smtpd
#smtp inet n - - - 1 postscreen
#smtpd pass - - - - - smtpd
#dnsblog unix - - - - 0 dnsblog
#tlsproxy unix - - - - 0 tlsproxy
submission inet n - - - - smtpd
-o syslog_name=postfix/submission
-o smtpd_tls_security_level=encrypt
-o smtpd_sasl_auth_enable=yes
-o smtpd_client_restrictions=permit_sasl_authenticated,reject
-o milter_macro_daemon_name=ORIGINATING
smtps inet n - - - - smtpd
-o syslog_name=postfix/smtps
-o smtpd_tls_wrappermode=yes
-o smtpd_sasl_auth_enable=yes
-o smtpd_client_restrictions=permit_sasl_authenticated,reject
-o milter_macro_daemon_name=ORIGINATING
#628 inet n - - - - qmqpd
pickup unix n - - 60 1 pickup
cleanup unix n - - - 0 cleanup
qmgr unix n - n 300 1 qmgr
#qmgr unix n - n 300 1 oqmgr
tlsmgr unix - - - 1000? 1 tlsmgr
rewrite unix - - - - - trivial-rewrite
bounce unix - - - - 0 bounce
defer unix - - - - 0 bounce
trace unix - - - - 0 bounce
verify unix - - - - 1 verify
flush unix n - - 1000? 0 flush
proxymap unix - - n - - proxymap
proxywrite unix - - n - 1 proxymap
smtp unix - - - - - smtp
relay unix - - - - - smtp
# -o smtp_helo_timeout=5 -o smtp_connect_timeout=5
showq unix n - - - - showq
error unix - - - - - error
retry unix - - - - - error
discard unix - - - - - discard
local unix - n n - - local
virtual unix - n n - - virtual
lmtp unix - - - - - lmtp
anvil unix - - - - 1 anvil
scache unix - - - - 1 scache
#
# ====================================================================
# Interfaces to non-Postfix software. Be sure to examine the manual
# pages of the non-Postfix software to find out what options it wants.
#
# Many of the following services use the Postfix pipe(8) delivery
# agent. See the pipe(8) man page for information about ${recipient}
# and other message envelope options.
# ====================================================================
#
# maildrop. See the Postfix MAILDROP_README file for details.
# Also specify in main.cf: maildrop_destination_recipient_limit=1
#
maildrop unix - n n - - pipe
flags=DRhu user=vmail argv=/usr/bin/maildrop -d ${recipient}
#
# ====================================================================
#
# Recent Cyrus versions can use the existing "lmtp" master.cf entry.
#
# Specify in cyrus.conf:
# lmtp cmd="lmtpd -a" listen="localhost:lmtp" proto=tcp4
#
# Specify in main.cf one or more of the following:
# mailbox_transport = lmtp:inet:localhost
# virtual_transport = lmtp:inet:localhost
#
# ====================================================================
#
# Cyrus 2.1.5 (Amos Gouaux)
# Also specify in main.cf: cyrus_destination_recipient_limit=1
#
#cyrus unix - n n - - pipe
# user=cyrus argv=/cyrus/bin/deliver -e -r ${sender} -m ${extension} ${user}
#
# ====================================================================
# Old example of delivery via Cyrus.
#
#old-cyrus unix - n n - - pipe
# flags=R user=cyrus argv=/cyrus/bin/deliver -e -m ${extension} ${user}
#
# ====================================================================
#
# See the Postfix UUCP_README file for configuration details.
#
uucp unix - n n - - pipe
flags=Fqhu user=uucp argv=uux -r -n -z -a$sender - $nexthop!rmail ($recipient)
#
# Other external delivery methods.
#
ifmail unix - n n - - pipe
flags=F user=ftn argv=/usr/lib/ifmail/ifmail -r $nexthop ($recipient)
bsmtp unix - n n - - pipe
flags=Fq. user=bsmtp argv=/usr/lib/bsmtp/bsmtp -t$nexthop -f$sender $recipient
scalemail-backend unix - n n - 2 pipe
flags=R user=scalemail argv=/usr/lib/scalemail/bin/scalemail-store ${nexthop} ${user} ${extension}
mailman unix - n n - - pipe
flags=FR user=list argv=/usr/lib/mailman/bin/postfix-to-mailman.py
${nexthop} ${user}
Dovecot
Creamos el fichero dovecot-mysql.conf.ext
root@mail-nusepas:/etc/dovecot# vi dovecot-mysql.conf.ext driver = mysql connect = host=localhost dbname=postix user=postfix_ro password=YYY default_pass_scheme = MD5-CRYPT user_query = SELECT '/var/mail/%d/%n' as home, 4001 AS uid, 4001 AS gid FROM mailbox WHERE username = '%u' password_query = SELECT password FROM mailbox WHERE username = '%u'
root@mail-nusepas:/etc/dovecot# vi conf.d/10-auth.conf disable_plaintext_auth = yes auth_mechanisms = plain login #!include auth-system.conf.ext !include auth-sql.conf.ext
root@mail-nusepas:/etc/dovecot# vi conf.d/10-mail.conf mail_location = maildir:/var/mail/%d/%n:INDEX=/var/mail/%d/%n/indexes
root@mail-nusepas:/etc/dovecot# vi conf.d/10-ssl.conf ssl = yes ssl_cert = /etc/letsencrypt/live/mail.nusepas.com/fullchain.pem ssl_key = /etc/letsencrypt/live/mail.nusepas.com/privkey.pem
root@mail-nusepas:/etc/dovecot# vi conf.d/20-imap.conf
protocol imap {
mail_max_userip_connections = 10
}
root@mail-nusepas:/etc/dovecot# vi conf.d/auth-sql.conf.ext
passdb {
driver = sql
# Path for SQL configuration file, see example-config/dovecot-sql.conf.ext
args = /etc/dovecot/dovecot-mysql.conf.ext
}
userdb {
driver = sql
args = /etc/dovecot/dovecot-mysql.conf.ext
}
root@mail-nusepas:/etc/dovecot# vi conf.d/10-master.conf
service lmtp {
unix_listener /var/spool/postfix/private/dovecot-lmtp {
mode = 0600
user = postfix
group = postfix
}
}
service auth {
# Postfix smtp-auth
unix_listener /var/spool/postfix/private/auth {
mode = 0666
}
}
Ahora reiniciamos los servicios y verificamos que no salen errores
root@mail-nusepas:/etc/dovecot# service dovecot restart root@mail-nusepas:/etc/dovecot# service postfix restart
SPAMASSASSIN
Instalamos spamassassin y spamc que es un cliente de spamassassin
root@mail-nusepas:~# apt install spamassassin spamc
Añadimos las siguientes líneas en el archivo /etc/postfix/master.cf
#
# Postfix master process configuration file. For details on the format
# of the file, see the master(5) manual page (command: "man 5 master" or
# on-line: http://www.postfix.org/master.5.html).
#
# Do not forget to execute "postfix reload" after editing this file.
#
# ==========================================================================
# service type private unpriv chroot wakeup maxproc command + args
# (yes) (yes) (yes) (never) (100)
# ==========================================================================
smtp inet n - - - - smtpd
-o content_filter=spamassassin
#smtp inet n - - - 1 postscreen
#smtpd pass - - - - - smtpd
#dnsblog unix - - - - 0 dnsblog
#tlsproxy unix - - - - 0 tlsproxy
submission inet n - - - - smtpd
-o syslog_name=postfix/submission
-o smtpd_tls_security_level=encrypt
-o smtpd_sasl_auth_enable=yes
-o smtpd_client_restrictions=permit_sasl_authenticated,reject
-o milter_macro_daemon_name=ORIGINATING
-o content_filter=spamassassinsend
smtps inet n - - - - smtpd
-o syslog_name=postfix/smtps
-o smtpd_tls_wrappermode=yes
-o smtpd_sasl_auth_enable=yes
-o smtpd_client_restrictions=permit_sasl_authenticated,reject
-o milter_macro_daemon_name=ORIGINATING
-o content_filter=spamassassinsend
#628 inet n - - - - qmqpd
pickup unix n - - 60 1 pickup
cleanup unix n - - - 0 cleanup
qmgr unix n - n 300 1 qmgr
#qmgr unix n - n 300 1 oqmgr
tlsmgr unix - - - 1000? 1 tlsmgr
rewrite unix - - - - - trivial-rewrite
bounce unix - - - - 0 bounce
defer unix - - - - 0 bounce
trace unix - - - - 0 bounce
verify unix - - - - 1 verify
flush unix n - - 1000? 0 flush
proxymap unix - - n - - proxymap
proxywrite unix - - n - 1 proxymap
smtp unix - - - - - smtp
relay unix - - - - - smtp
# -o smtp_helo_timeout=5 -o smtp_connect_timeout=5
showq unix n - - - - showq
error unix - - - - - error
retry unix - - - - - error
discard unix - - - - - discard
local unix - n n - - local
virtual unix - n n - - virtual
lmtp unix - - - - - lmtp
anvil unix - - - - 1 anvil
scache unix - - - - 1 scache
smtp-ipv4 unix - - - - - smtp
-o inet_protocols=ipv4
spamassassinsend unix - n n - - pipe
user=debian-spamd argv=/usr/bin/spamc -f -e /usr/sbin/sendmail -oi -f ${sender} ${recipient}
spamassassin unix - n n - - pipe
flags=DROhu user=vmail:vmail argv=/usr/bin/spamc -f -e /usr/lib/dovecot/deliver -f ${sender} -d ${user}@${nexthop}
root@mail-nusepas:~# vi /etc/spamassassin/local.cf rewrite_header Subject *****SPAM*****
Guardar Spam en SPAM
Configuramos que todos los correos se almacenen en una carpeta llamada SPAM
root@mail-nusepas:~# vi /etc/postfix/main.cf spamassassin_destination_recipient_limit = 1
Instalamos dovecot-sieve y lo configuramos
root@mail-nusepas:~# apt install dovecot-sieve
root@mail-nusepas:~# vi /etc/dovecot/conf.d/15-mailboxes.conf
mailbox Junk {
special_use = Junk
}
root@mail-nusepas:~# vi /etc/dovecot/conf.d/90-sieve.conf
plugin {
#sieve = file:~/sieve;active=~/.dovecot.sieve
}
root@mail-nusepas:~# vi /etc/dovecot/conf.d/90-plugin.conf
plugin {
sieve = /etc/dovecot/sieve/default.sieve
}
root@mail-nusepas:~# vi /etc/dovecot/conf.d/15-lda.conf
protocol lda {
# Space separated list of plugins to load (default is global mail_plugins).
mail_plugins = $mail_plugins quota sieve
postmaster_address = [email protected]
}
root@mail-nusepas:~# vi /etc/dovecot/conf.d/20-lmtp.conf
protocol lmtp {
mail_plugins = $mail_plugins sieve
}
root@mail-nusepas:~# mkdir /etc/dovecot/sieve/
root@mail-nusepas:~# vi /etc/dovecot/sieve/default.sieve
require "fileinto";
if header :contains "X-Spam-Flag" "YES" {
fileinto "INBOX.Junk";
}
root@mail-nusepas:~# chown vmail:vmail /etc/dovecot/sieve/ -R root@mail-nusepas:~# service postfix restart root@mail-nusepas:~# service dovecot restart root@mail-nusepas:~# service spamassassin restart
Fail2ban
Un poco de seguridad ante intentos de acceso al servidor por parte de robots
root@mail-nusepas:~# apt install fail2ban root@mail-nusepas:~# vi /etc/fail2ban/jail.conf [postfix] #port = smtp,465,submission #logpath = %(postfix_log)s #backend = %(postfix_backend)s enabled = true port = smtp,ssmtp,submission filter = postfix logpath = /var/log/mail.log root@mail-nusepas:~# service fail2ban restart
Configurar dominios
Entramos en postfixadmin y creamos el primer dominio, en éste caso nusepas.com y también creamos el buzón.
Aquí ya podemos mandar correos electrónicos al servidor. Si probamos de mandar uno al dominio y cuenta que hayamos creado veremos que en syslog entra un correo electrónico y queda almacenado en /var/mail/nusepas.com/admin/
RoundCube
Ahora configuraremos roundcube. Pero primero tenemos que crear una base de datos nueva para roundcube
MariaDB [(none)]> create database roundcube; Query OK, 1 row affected (0.00 sec) MariaDB [(none)]> GRANT ALL PRIVILEGES ON roundcube.* TO 'roundcube_admin'@'localhost' IDENTIFIED BY 'ZZZ'; Query OK, 0 rows affected (0.00 sec) MariaDB [(none)]> flush privileges; Query OK, 0 rows affected (0.00 sec)
a continuación lo desplegaremos los ficheros de roundcube en algún sitio (por ejemplo en /var/www/html/) e iremos al instalador via web
https://mail.nusepas.com/roundcubemail/installer/
Tendremos que resolver todas las dependencias que nos pide
root@mail-nusepas:~# apt install php-xml php-intl php-imagick php-gd php-ldap root@mail-nusepas:~# dpkg-reconfigure tzdata Current default time zone: 'Europe/Madrid' Local time is now: Sat Oct 20 18:20:43 CEST 2018. Universal Time is now: Sat Oct 20 16:20:43 UTC 2018. root@mail-nusepas:~# vi /etc/php/7.0/apache2/php.ini date.timezone = "Europe/Madrid" root@mail-nusepas:~# service apache2 restart
Ahora rellenamos todos los datos que nos pida y si todo va bien podremos entrar en nuestro webmail.
PS: ahora no me está autenticando IMAP, pero recibo correos. A la que tenga la solución actualizo el post…
Fuente: https://alquimistadesistemas.com/instalar-sasl-postfixpostfixadmindovecot-y-filtros-de-spam-en-debian.html

3 respuestas
Hi friends,
I’m having trouble after following your guide. I’m configure an email account with imap and try to send an email, it tells me the following message «Your message was sent but a copy was not placed in the sent folder (Sent)»
No errors are seen from the server.
Can you help me?
Thanks
Check if you dovecot.conf have this config rules, (Respect the Upper Cases):
namespace inbox {
inbox = yes
separator = .
mailbox Drafts {
special_use = \Drafts
}
mailbox Junk {
special_use = \Junk
}
mailbox Sent {
special_use = \Sent
}
mailbox «Sent Messages» {
special_use = \Sent
}
mailbox Trash {
special_use = \Trash
}
}
I’m check the dovecot.conf and have this config rules
my dovecot -n is :
# Pigeonhole version 0.5.4 ()
# OS: Linux 4.19.0-16-amd64 x86_64 Debian 10.9 ext4
# Hostname: mail.xxxxx.com
auth_debug = yes
auth_debug_passwords = yes
auth_mechanisms = plain login
auth_verbose = yes
auth_verbose_passwords = yes
debug_log_path = /var/log/dovecot-debug
log_path = /var/log/dovecot
mail_debug = yes
mail_location = maildir:/var/mail/%d/%n:INDEX=/var/mail/%d/%n/indexes
mail_privileged_group = mail
namespace inbox {
inbox = yes
location =
mailbox Drafts {
special_use = \Drafts
}
mailbox Enviados {
special_use = \Sent
}
mailbox Junk {
special_use = \Junk
}
mailbox Sent {
special_use = \Sent
}
mailbox «Sent Messages» {
special_use = \Sent
}
mailbox Trash {
special_use = \Trash
}
prefix =
separator = .
}
passdb {
args = /etc/dovecot/dovecot-mysql.conf.ext
driver = sql
}
plugin {
sieve = file:~/sieve;active=~/.dovecot.sieve
}
protocols = » imap lmtp pop3 lmtp»
service auth-worker {
user = vmail
}
service auth {
unix_listener /var/spool/postfix/private/auth {
group = postfix
mode = 0666
user = postfix
}
unix_listener auth-userdb {
mode = 0600
user = vmail
}
user = dovecot
}
service lmtp {
unix_listener /var/spool/postfix/private/dovecot-lmtp {
group = postfix
mode = 0600
user = postfix
}
}
service stats {
unix_listener stats-reader {
group = vmail
mode = 0660
user = vmail
}
unix_listener stats-writer {
group = vmail
mode = 0660
user = vmail
}
}
ssl_cert = </etc/letsencrypt/live/mail.xxxxx.com/fullchain.pem
ssl_client_ca_dir = /etc/ssl/certs
ssl_dh = # hidden, use -P to show it
ssl_key = # hidden, use -P to show it
userdb {
args = /etc/dovecot/dovecot-mysql.conf.ext
driver = sql
}
protocol lmtp {
mail_plugins = " sieve"
}
protocol lda {
mail_plugins = " quota sieve"
postmaster_address = [email protected]
}
protocol imap {
mail_max_userip_connections = 10
}
I can't find the error