Vulnerability Trends Summary
As part of our monthly vulnerability trends, this report shows the monthly top 10 trends on security vulnerabilities and how hackers, malware, and exploit kits are exploiting those vulnerabilities. To demonstrate, we assign vulnerability trends value as a percentage of how each vulnerability is significantly gaining the attention of cybersecurity communities, attackers, together with malware. In either case, companies can benefit from the report to have more cyber threat insights and relatively anticipate attacks wave that might target their public assets in the following months.
Subscribe to the monthly vulnerability digest report by clicking here.
Download the full vulnerability digest report by clicking here.
The following chart shows the trends.
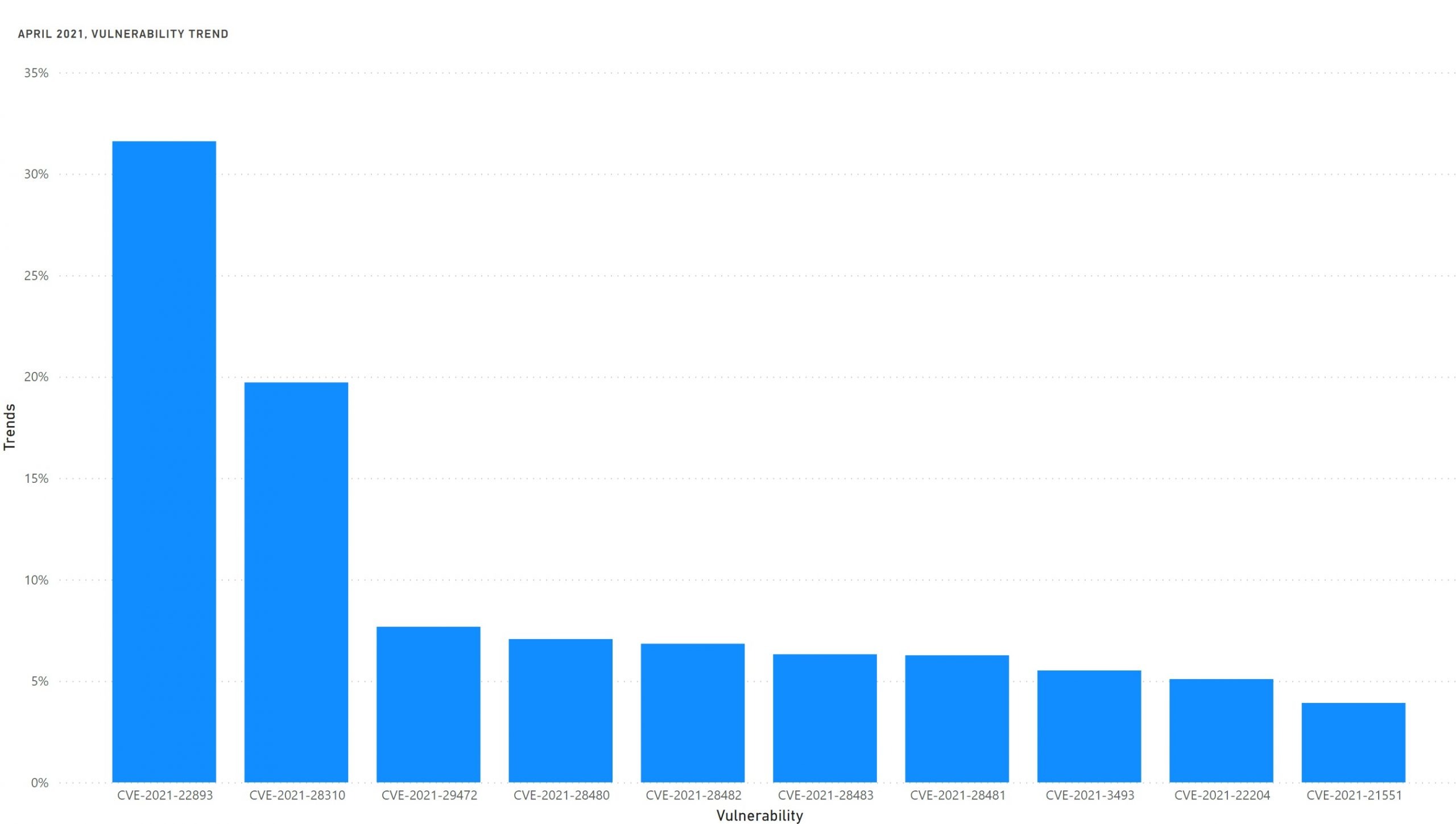
April 2021 was a relief for system admins as less critical vulnerabilities compared to previous months. Pulse Secure authentication bypass was the vulnerability of the month. The next in line is Windows Kernel privilege escalation which is currently being exploited by attackers.
Other critical and important vulnerabilities were discovered in MS Exchange Server, Composer, Dell Driver, and Linux Kernel.
The following table shows the details of the trends.
| CVE | Vulnerability | Publish Date | Exploited | Trends* |
| CVE-2021-22893 | Pulse Secure authentication bypass | 20/04/2021 | Yes | 32% |
| CVE-2021-28310 | Privilege escalation in Windows Kernel | 13/04/2021 | Yes | 20% |
| CVE-2021-29472 | Command injection in Composer | 27/04/2021 | Yes | 8% |
| CVE-2021-28480 | Remote Code Execution in Microsoft Exchange | 13/04/2021 | No | 7% |
| CVE-2021-28482 | Remote Code Execution in Microsoft Exchange | 13/04/2021 | Yes | 6% |
| CVE-2021-28483 | Remote Code Execution in Microsoft Exchange | 13/04/2021 | No | 6% |
| CVE-2021-28481 | Remote Code Execution in Microsoft Exchange | 13/04/2021 | No | 6% |
| CVE-2021-3493 | Privilege escalation in Linux Kernel | 16/04/2021 | Yes | 6% |
| CVE-2021-22204 | Code execution in ExifTool | 23/04/2021 | Yes | 5% |
| CVE-2021-21551 | Privilege escalation in Dell Driver | 05/04/2021 | Yes | 4% |
Subscribe to the monthly vulnerability digest report by clicking here.
Download the full vulnerability digest report by clicking here.
1. CVE-2021-22893 Pulse Secure Authentication Bypass
Pulse Connect Secure is vulnerable to an authentication bypass vulnerability exposed by the Windows File Share Browser and Pulse Secure Collaboration features of Pulse Connect Secure that can allow an unauthenticated user to perform remote arbitrary code execution on the Pulse Connect Secure gateway.
2. CVE-2021-28310 Win32k Privilege Escalation
Privilege escalation vulnerability in Windows kernel (Win32k) due to out-of-bounds (OOB) write issue in dwmcore.dll, which is part of Desktop Window Manager (dwm.exe).
3. CVE-2021-29472 Composer Command Injection
Command injection vulnerability exists in Composer the PHP library manager which allows supply chain attack to be successful.
4. CVE-2021-28480 Remote Code Execution in Exchange Server
Remote code execution vulnerability exists in Microsoft Exchange Server. By sending a special request to the server, an attacker is able to execute arbitrary code on the server. This vulnerability is unique from CVE-2021-28482, CVE-2021-28481, and CVE-2021-28483.
5. CVE-2021-28482 Remote Code Execution in Exchange Server
Remote code execution vulnerability exists in Microsoft Exchange Server. By sending a special request to the server, an attacker is able to execute arbitrary code on the server. This vulnerability is unique from CVE-2021-28480, CVE-2021-28481, and CVE-2021-28483.
6. CVE-2021-28483 Remote Code Execution in Exchange Server
Remote code execution vulnerability exists in Microsoft Exchange Server. By sending a special request to the server, an attacker is able to execute arbitrary code on the server. This vulnerability is unique from CVE-2021-28480, CVE-2021-28481, and CVE-2021-28482.
7. CVE-2021-28481 Remote Code Execution in Exchange Server
Remote code execution vulnerability exists in Microsoft Exchange Server. By sending a special request to the server, an attacker is able to execute arbitrary code on the server. This vulnerability is unique from CVE-2021-28480, CVE-2021-28482, and CVE-2021-28483.
8. CVE-2021-3493 Privilege Escalation in Linux Kernel
Local privilege escalation vulnerability exists in Linux kernel as overlayfs implementation did not properly validate with respect to user namespaces the setting of file capabilities on files in an underlying file system.
9. CVE-2021-22204 Command Execution in ExifTool
Improper neutralization of user data in the DjVu file format in ExifTool allows arbitrary code execution when parsing the malicious image.
10. CVE-2021-21551 Privilege Escalation in Dell Driver
Dell dbutil_2_3.sys driver contains an insufficient access control vulnerability which may lead to escalation of privileges, denial of service, or information disclosure. Local authenticated user access is required.
Fuente obtenida de: https://scantitan.com/blog/monthly-vulnerability-digest/vulnerability-trends-april-2021-2/